This specialized utility provides forensic investigators and researchers with a framework for extracting digital artifacts from volatile memory samples.
Volatility
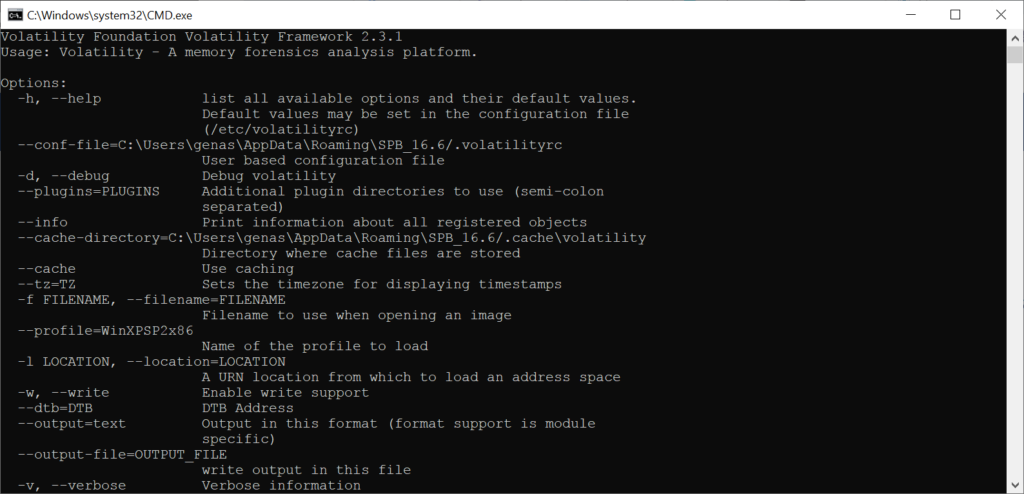
Volatility is a command line Windows program that gives users tools for recovering data from memory dumps, which is crucial for forensic analysis. It supports a wide variety of target operating systems, including Linux and MacOS.
Brief overview
Using this tool you can analyze volatile memory samples and potentially restore information that was stored on source RAM modules. The operation is performed without relying on the specific file system to ensure that results are not influenced by external factors.
Volatility is built entirely in Python and accessible for modification or customization. Moreover, its modular design allows users to integrate third party libraries into the workflow, expanding basic capabilities.
Data analysis
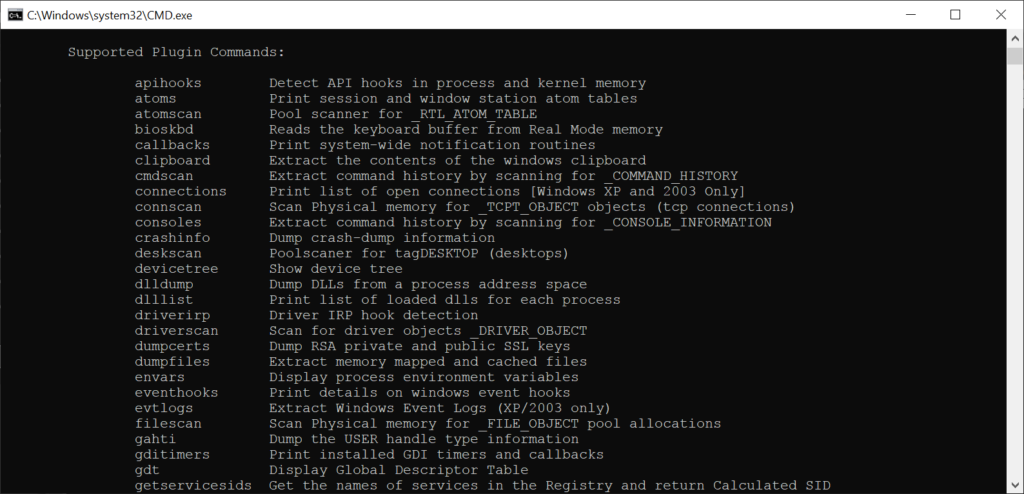
There are instruments to uncover hidden processes, malware activity and unauthorized system changes on the target device. This helps you conduct cybercrime investigations and track persistent threats across multiple computers.
Professional researchers can use the application to explore innovative methods of memory analysis and incident response. Additionally, it is possible to facilitate the testing and validation of new forensic techniques.
Features
- free to download and use;
- helps you collect information from memory dumps;
- prevents accidental file modification to ensure data integrity;
- users can identify malware infections and view active processes;
- compatible with all modern versions of Windows.